Sophisticated Phishing Scam Uses a Combination Malicious Code, a Fake Domain Name, and a Russian Payment System
Fake domain names are commonly used by threat actors to deceive users at the point of sale (like registering a fake website). Recently we helped take down an aggressive attack on a client scam that combined a typosquatting domain name with a code-injection attack, plus a fake (but functional) payments page to create an extremely effective scam.
WHAT HAPPENED:
As with most online scams, the threat actor registered several fake (typo-squatted) domain names. Then, they managed to inject malicious code into the client’s online payments page. And the third part of the scam was a replica Stripe/Shopify payment screen.
The threat actor then used the infected code to track each time the client’s system was used to complete a sale. While the personally identifiable information (PII) remained safe from the threat actor, the injected code was able to exfiltrate the email address of each customer who completed a transaction in real time.
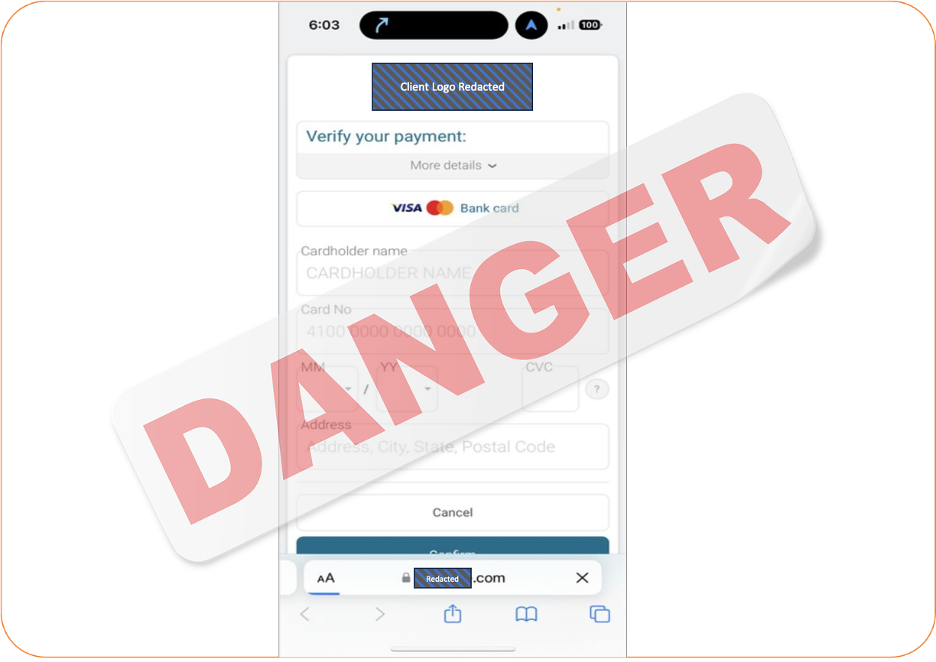
Immediately after the purchase, the customer received an email claiming that the customer’s payment was “suspicious”, and required further verification or the order would be canceled. Of course, the link in the email to ‘verify the order’ sent the customer to a fake payment page with instructions to re-enter the card information. Of course the email used a typosquatting domain for the ‘from’ address, and the look and feel was a perfect match to the clients brand.
THE ALARM:
The first sign of the scam appeared in the client’s DomainSkate dashboard when a domain name tied to a Russian payment system, using a typosquatting domain, popped up. The domain redirected to a website at a .RU ccTLD that is known as PayMaster (screenshot below). Our system automatically notified our client.
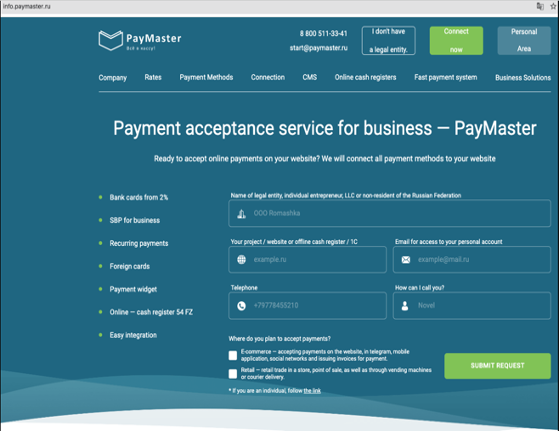
At first glance, there was nothing that appeared “malicious” about the domain, and nothing on the site that would raise immediate suspicion, or tie the client to anything happening at PayMaster. So, the domain was placed on DomainSkate’s watchlist for daily updates.
One day after DomainSkate’s notification, the client began receiving messages from customers

The message was sent with an embedded “Verification” button at the bottom. This button was a quick link that (once clicked) created a checkout pop-up, that looked like a typical Shopify or Stripe checkout portal. The only tell-tale sign that the pop-up was not legitimate was the domain that appeared on the bottom of the checkout tab – that domain was the exact domain name that had appeared in the client’s dashboard and redirected to the PayMaster site. This was proof of a scam.
HOW DOMAINSKATE SHUT DOWN THE ATTACK:
We immediately recommended a triage of the client’s code and found that there was malicious code in the client’s system sending this message to any/all customers that were buying a product on its website.
Also, we immediately recommended removing the code from the client’s system and a takedown of the domain that was being used to perpetuate this scam. DomainSkate has also started a forensic analysis into any/all redirects in our system that have a PayMaster.ru domain.
WHAT SHOULD YOU DO:
Going forward, we have recommended that all clients flag the PayMaster.ru domain, and have set up automatic warnings and checks in our system if there is a direct or redirect connection to a PayMaster.ru domain. If you have had this issue or have questions about this case please contact us at:
Authors: David Mitnick and David W. Schropfer