Find out how Law Firms increase billable hours and client retention with DomainSkate.
Learn how our AI-supported threat intelligence feeds expose the problem, and provide solutions.
See how eCommerce and other Retail companied save millions protecting their brand with DomainSkate.
Avoid lawsuts and reguatory fines by diligently finding, monitoring, and shutting down fake websites.
Deliver predictive threat intelligence data directly from our platform to yours integrated via Webhooks and APIs.
With our concerge service, we do all of the work for you! One of our experts will monitor your account every day, and if we thin something should be shut down, we call you.
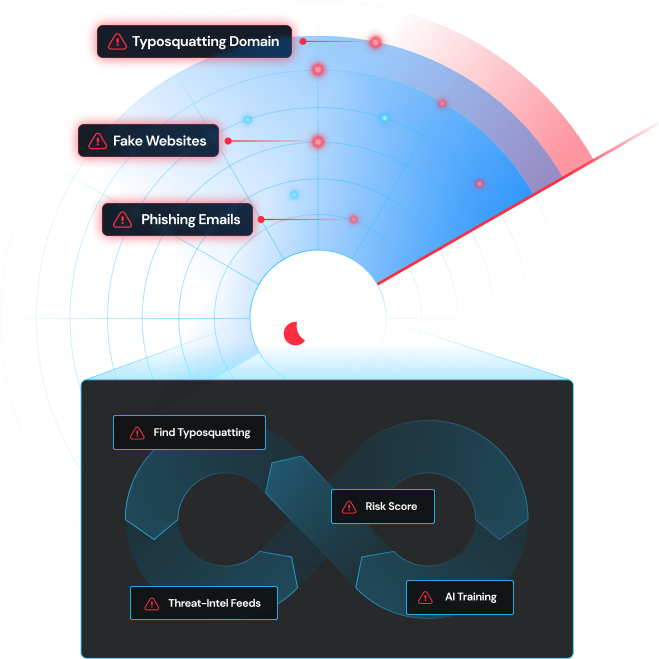
DomainSkate’s DomainSkate Professional monitors domain registrations, analyzes phishing websites, identifies typo squatting domains, and maintains a domain watchlist.
Everything from DomainSkate Professional, and we include 50 takedowns per brand per year!
DomainSkate offers flexible pricing plans tailored to businesses of all sizes. Plans range from basic monitoring for small businesses to advanced threat intelligence for larger enterprises.
DomainSkate stands out with lower pricing and superior effectiveness, offering robust domain monitoring and advanced threat detection. Designed for small and medium-sized businesses
We offer easy-to-use APIs to utilize and integrate our available services into other systems.
Dive into a world of expertise with our webinar videos. Explore insights, trends, and practical tips from industry experts.
FInd a wealth of expertise through our blog posts. Discover insights, trends, and practical tips from industry experts.
Get a free market study that uses DomainSkate’s proprietary data, with comments and analysis by industry researchers.
Find out the story behind the company that top compnies trust to protect their brands on the internet.
See our seasoned professionals who bring you the best-in-class, most afforable brand protection software platform in the industry.
Interested in becoming a DomainSkate partner? Click here to find out more.
See our current open positions, and join our world-class team!
Contact our team, and get a map to our New York City offices.